Install cert-manager in a GKE cluster to use with let’s Encrypt
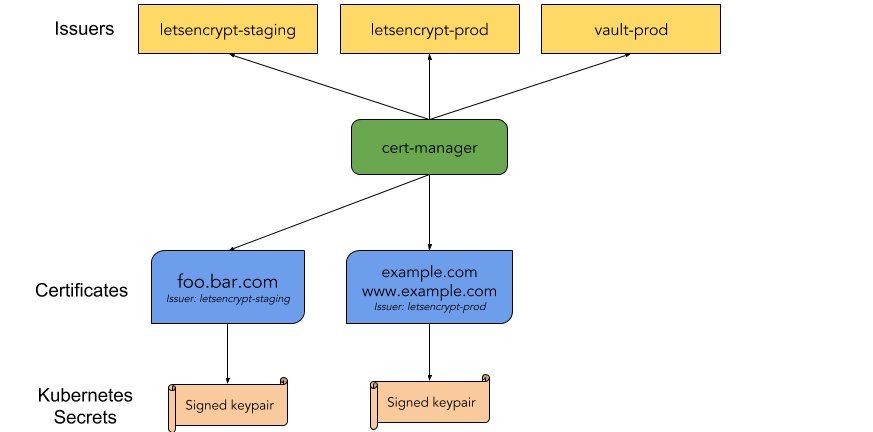
Cert-manager automates the management and issuance of TLS certificates from various issuing sources. It extends Kubernetes with a Custom Resource. You may use it with Let’s encrypt which is a free issuer.
1 – Installation
# Install the CustomResourceDefinition resources separately
kubectl apply -f \
https://raw.githubusercontent.com/jetstack/cert-manager/release-0.6/deploy/manifests/00-crds.yaml
# Create a namespace to run cert-manager in
kubectl create namespace cert-manager
# Disable resource validation on the cert-manager namespace
kubectl label namespace cert-manager \
certmanager.k8s.io/disable-validation=true
# Update your local Helm chart repository cache
helm repo update
# Install the cert-manager Helm chart
helm install --name cert-manager --namespace cert-manager \
--version v0.6.5 stable/cert-manager
There is currently an issue with GKE and the v0.6.5 version of cert-manager. It has been fixed in the v0.7.0-beta.0 release of cert-manager. This release has moved to the jetstark repository.
helm repo add jetstack https://charts.jetstack.io
helm upgrade cert-manager --version v0.7.0-beta.0 \
jetstack/cert-manager
2 – Issuer
To be able to get certificates for your backend services you need to add an Issuer or a ClusterIssuer to your cluster. Here we choose to define a ClusterIssuer which is not tight to a particular namespace in the cluster. We choose also to use let’s encrypt CA with the http challenge for the ACME registration.
Staging issuer
Since you don’t want to exceed the 50 let’s encrypt certificates quota you”ll prefer to use this cluster issuer in development mode:
# This clusterIssuer example uses the staging environment for testing first
apiVersion: certmanager.k8s.io/v1alpha1
kind: ClusterIssuer
metadata:
name: letsencrypt-staging
spec:
acme:
# Email address used for ACME registration
email: mail@example.com
# Enable the HTTP-01 challenge provider
http01: {}
# Name of a secret used to store the ACME account private key
privateKeySecretRef:
name: letsencrypt-staging
# The ACME server URL
server: https://acme-staging-v02.api.letsencrypt.org/directory
Production issuer
Define also the production issuer to use when everything is fine:
apiVersion: certmanager.k8s.io/v1alpha1
kind: ClusterIssuer
metadata:
name: letsencrypt-prod
spec:
acme:
# The ACME server URL
server: https://acme-v02.api.letsencrypt.org/directory
# Email address used for ACME registration
email: mail@example.com
# Name of a secret used to store the ACME account private key
privateKeySecretRef:
name: letsencrypt-prod
# Enable the HTTP-01 challenge provider
http01: {}